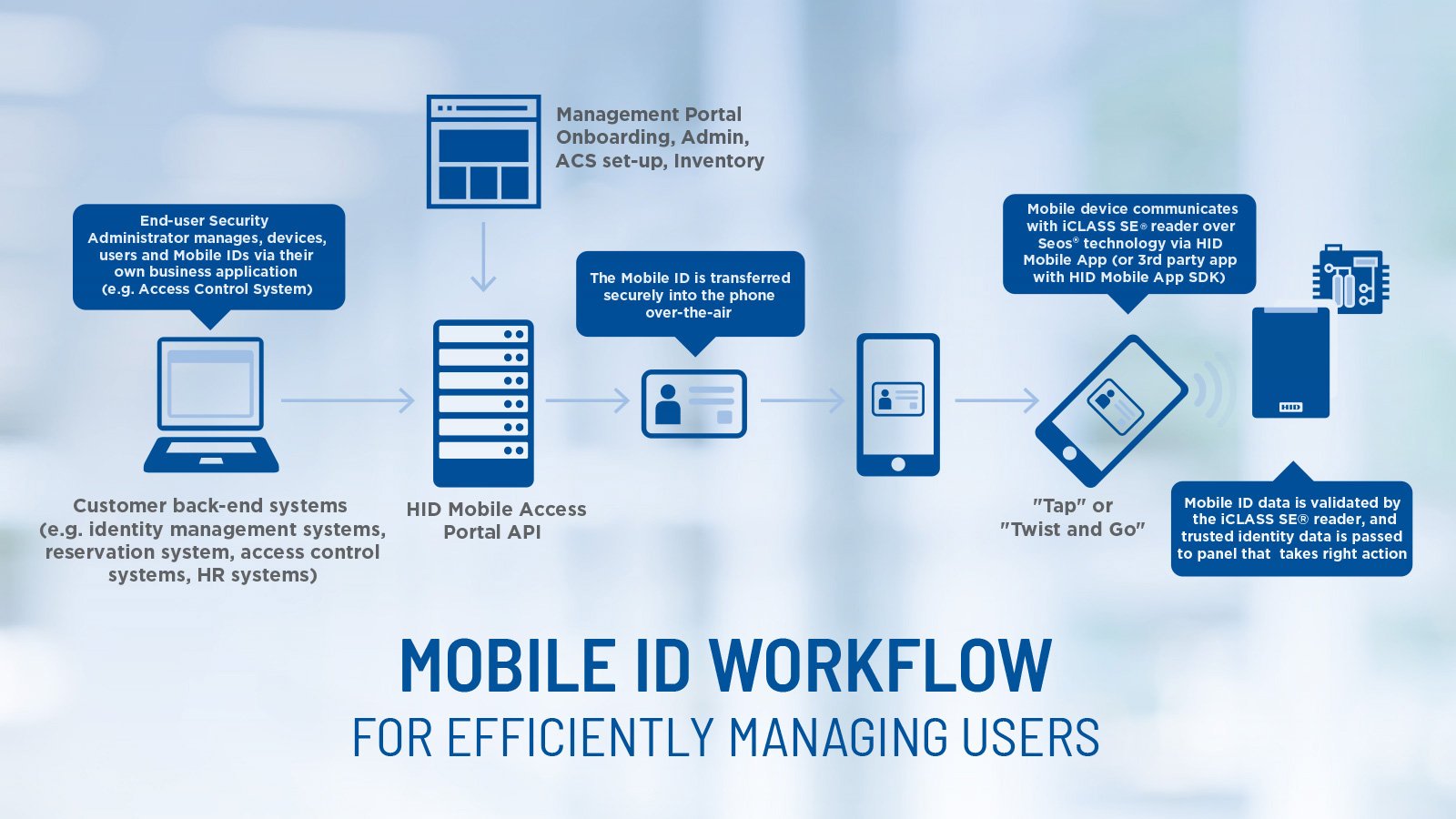
Access card technology has evolved from Swipe to B.Y.O.D. The following timeline illustrates how access control technology has changed and the new technology available.
Access card technology has evolved from Swipe to B.Y.O.D. The following timeline illustrates how access control technology has changed and the new technology available. If you would like more information, please download the full executive brief by HID Global here.
.png?width=580&height=852&name=Progression%20of%20access%20control%20(cropped).png) Download the timeline infographic here
Download the timeline infographic here
1980s — Swipe Technologies: Initial swipe technologies were an improvement over the standard manual locks. Swipe technologies offered efficient administration, management, and traceability of the key cards. Knowing and controlling access rights to specific areas removed the need to re-key as employees left or changed roles in the organization.
1990s – “Prox”: In time, the limitations of swipe technologies were felt. Users found the need for physical contact between readers and credentials to be burdensome. Additionally, physical wear on the cards and readers became costly and time-consuming for administrators. Thus, the emergence of contactless technologies was revolutionary in the access control industry. Prox cards featured the first “low- frequency proximity technology” allowing for the card data to be detected a few inches from the reader. This technology decreased maintenance costs and increased user convenience.
Late 1990s-2010s — First-Generation Contactless Smart Cards: Around 2000, contactless smart cards emerged that offered more sophisticated technology than Prox. These smart cards, including brands such as MIFARE® and iCLASS®, utilized high-frequency technology (13.56MHz) and featured new credentials. They also addressed the two main limitations of Prox cards: unencrypted credentials and the inability to encode the card with multiple IDs. First, the contactless smart cards and the readers could mutually authenticate every transaction. Second, these cards could store more information than just an ID number, such as a cashless vending debit value or a biometric data. This allowed for an increase in security/data privacy and multi-application functionality. Despite these benefits, most first-generation smart cards have vulnerabilities in the mutual authentication algorithms making it possible for hackers to forge or clone credentials.
2013-Present — Second-Generation Contactless Smart Cards: Earlier this decade, contactless smart cards evolved further to meet the needs of today’s businesses better. Second-generation contactless smart cards differ from their predecessors in two key areas: security and applications. Today’s credentials are more secure due to a new industry protocol: open standards. These standards did not exist when first-generation smart cards were created. Open standards are regularly updated and adjusted enabling better protection for organizations. Second-generation cards also provide the user with a variety of applications. Administrators can create and manage secure identities on cards, but also on mobile devices and wearables through NFC and Bluetooth. Secure printing and cashless vending are examples of multiapplication use.
The Next Generation of Credentials — Mobile Devices: Mobile devices are ingrained into nearly every aspect of daily life. For access control, a new trend is established: bring your own device (BYOD). Allowing building users to use their smartphone or tablet to verify their credentials will likely supplement or replace cards.
Conclusion:
Cards and credential technologies have significantly advanced since they hit the market over 30 years ago. The transition from Magstripe to Prox introduced the concept of contactless technology. Contactless technology has evolved, and new generations of cards are more secure and can be used for a variety of applications. The future of access control will move towards the integration of mobile devices with the goal of increasing the functionality of access control systems. Only a modern ecosystem will be able to keep pace with the transformative trends today’s organizations are facing. Fortunately, upgrading your physical access control system is not as difficult as you may think.
Click the link below to speak with a representative and receive a free quote for access cards.