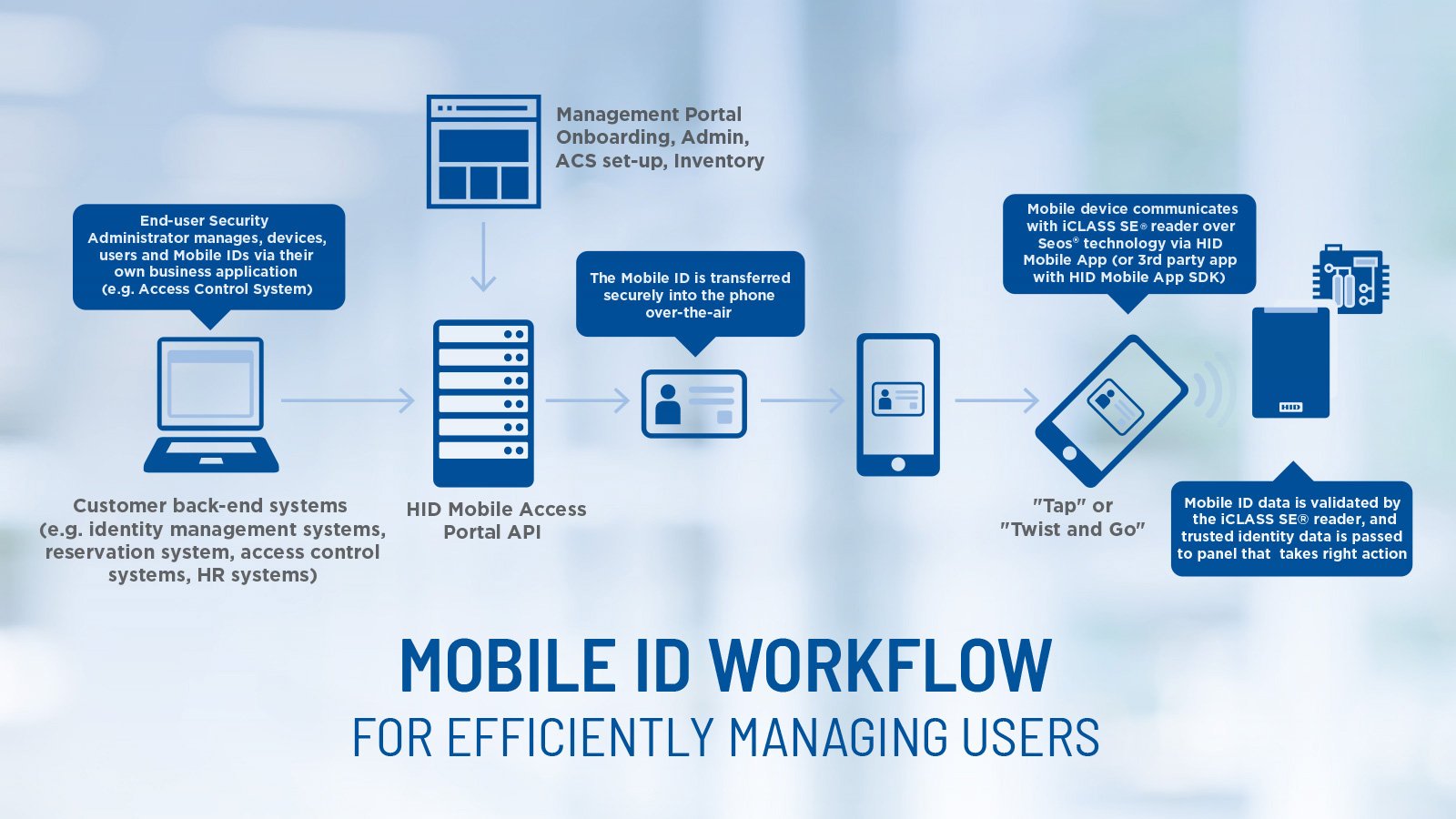
Organizations are increasingly adopting credential technology that can be used for multiple purposes to accommodate the needs of today’s mobile workforce. These include various combinations of physical and network access. This trend ultimately requires moving away from legacy systems and adopting the latest technology.
Four elements common to all access control solutions – and how they interact
Most physical access control systems consist of four basic elements:
- Credentials
- Readers
- Controllers
- Software Application
The Credential
Physical access credentials come in a variety of form factors – Smart Card, fob, mobile device, and others. They almost all carry a number, or set of numbers, that are used to identify the cardholder – usually a simple string of binary numbers (ones and zeros) often referred to as the payload. The way data is conveyed to the reader varies according to the technology involved. The way the data is configured is called the format.
Common credential technologies include:
- Magnetic Stripe (Legacy Technology)
- Low Frequency 125 kHz (Legacy Technology)
- High-Frequency 13.56MHz (Current standard)
- Ultra High Frequency
Occasionally, two or more of the above technologies are combined on a single form factor. The combination of outdated legacy technologies and the current industry standard of 13.56 MHz should only be employed as a short-term strategy. Decreased risk can only be assured by the adoption of the high-frequency standard.
Extra Secure: Credential & Reader Mutual Authentication
To protect against common vulnerabilities, including forgery, cloning, and spoofing, some contactless smartcards and mobile credentials have an additional security step called “mutual authentication.”
For this more secure method, both the credential and reader contain a set of cryptographic keys (like a password or a shared secret handshake). When the credential is presented to the reader, the two use a complex mathematic process to compare keys. If the keys match, the reader accepts. If the keys do not match, the transaction is terminated.
Best practices for mutual authentication:
- The underlying credential technology should leverage the latest security standards, which protects against vulnerabilities of most legacy credentials
- Cryptographic keys must be unique to the organization
- Treated as highly confidential and protected
- Preferably machines generated – not seen or accessed by people
- All devices containing keys should be stored and operate on secure platforms
- Chain-of-custody control and tracking established
The Reader
Some readers are designed to support just one technology, while others support an array of multi-technology configurations. The reader itself has no awareness of the makeup of the card data format, nor is it aware of any access privileges for the cardholder. That information exists only in the controller and host software.
Typical reader configurations include:
- What credential types can be read
- Type of encryption used
- LED and beeper behavior
- Whether there is a keypad
- When a credential is read
- When the optical tamper switch is enabled
The Controller
The controller is the only device in the system where the binary credential data format can be decoded and acted upon. When the controller receives the data from the reader, embedded firmware decides whether, or not to grant access. A typical sequence:
- Length of the data format: Does the length of the binary data match the format length the controller is expecting? If the data from the card is too long or too short, the controller will either ignore it completely or send an “access deny” message.
- Evaluation of format structure: If the length is acceptable, the controller then breaks the binary string down into its component parts:
- Parity Bits: The simplest form of error-detecting code. The controller determines if an error was made in the encoding, reading, or transmission of binary data.
- Facility & Site Codes: Does the Facility Code match an authorized value?
- Credential Number: Is the credential number in memory? Most controllers can store tens or hundreds of thousands of credential numbers locally.
- Access Rights Evaluated: Is the credential number authorized for this reader at this date and time?
Software
Every access control system has some form of user interface, usually a discrete PC application or web-based interface for operators to interact with the system. They will use it to:
- Add and delete cardholders
- Assign, modify, or delete access privileges
- Create and modify time schedules, holiday lists, etc.
- Configure system hardware for doors, alarm points, etc.
- Monitor system events in real-time
- Generate historical reports on all types of system activity
In most cases, the access system is fully automated and connected to the reader and door hardware via dedicated wiring.
Summary
- Adopting current industry standards over legacy technology reduces the risk
- Mutual authentication between reader and credential offers additional protection against cloning, spoofing, and forgery
- Understanding controller capabilities provide greater insight into how a system will perform with any given credential technology
- The host system is where access control rights are managed and maintained